“Your package has been sent, please check it”; “Your Facebook account has been compromised, please enter your credentials”; “The Ministry of Health recommends that you download TousAntiCovid”: Like me and like so many others, you may have received one of these text messages in recent months. A message that may have sown doubt in you: were they real messages, therefore with real issues (receiving / not missing a package, securing your Facebook account, protecting yourself from the Covid), or fake SMS? This doubt, you already had it for a long time by going through your mailbox. But now, phishing (“phishing”, in VF) is also exported by text message. And the current health crisis has seen a resurgence of this phenomenon, renamed for the occasion “smishing” (for SMS + phishing).
Fake text messages that multiply
In the case of the first example of fraudulent SMS, it is one of the many “parcel scams” currently on the rise. Inevitably, since the shops are closed or in any case less accessible, we have more recourse to delivery. And it is enough that the SMS is sufficiently well shot and that it is sent to you at the right time, for example when you are just waiting for a package, for you to bite the bait. With potentially disastrous consequences.
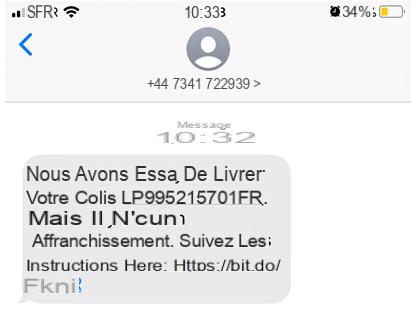
Behind this famous “parcel sent” to be checked, hides a very dangerous SMS phishing campaign. After clicking on the link in this message that claims you will soon receive a package, you will sometimes come across a copy of a real identification page, where you will be asked to fill in your real identifiers, for the worst and for the worse. You will also come across other times on a page where you are invited by devious means to install an app or an update. This app or update is obviously just malware, which once installed will give the hackers behind it access to your smartphone and its data.
Since April 2021, a fake SMS in the colors of FedEx, UPS, La Poste or Colissimo has been circulating. This message, which I myself received the same day that I was expecting an important parcel, follows the classic pattern of phishing e-mails related to parcel deliveries. It claims that the courier/delivery company needs you to tell them where you want to receive your package due to the unexpected - which, let's face it, could very well happen in the case of a real delivery. And it sends you back for this, via a short link, to a web page where there is a form. But this page does not display well, and a small insert then urges you to update your web browser (Chrome, in this case). The rest, you can imagine it well…
With the crisis, therefore, phishing is on the rise, and especially via SMS. The phenomenon has taken on such proportions that it prompted the Spanish authorities to recently issue a call for vigilance. The latest report from the Cybermalveillance.gouv.com platform, which lists the “big trends” in terms of “cyber threats”, explains that in 2020, “phishing campaigns by SMS have developed considerably”, because “this mode of communication is increasingly used by the various platforms to communicate directly with their users", and because at the same time, the latter "are much less suspicious when they receive an SMS, especially since it is more difficult to spot identity theft or a fraudulent site from an SMS on a phone than in an e-mail on your computer.”' In 2020, 17% of requests for help on the platform concerned phishing. This is the “No. 1 threat” for individuals.
Indeed: when it comes to an e-mail, we often have enough hindsight not to click. After all, we are behind a computer, and we are in a position that allows us to keep a cool head, and to guess that it is a virus or a scam. But when it happens by SMS, it's different: real deliveries increasingly use text messages, we have much less perspective when we are behind our smartphone, and scammers know it. They play on your fear of missing a package, and bet that you will rush into their trap. Knowing that on average, according to a German study, it is 45% of users who click on links received by e-mail or SMS, even when they do not know the source. “The use of SMS as a phishing medium will be a strong trend which will be confirmed and will certainly intensify in the coming years”, predicts the Cybermalveillance.gouv platform. According to her, “virtually professional” hacking kits are even offered for sale on “criminal forums”.
But don't panic: to avoid falling into the trap, you just need to know how to spot these fake SMS. This implies first of all understanding their modus operandi.
The Smishing modus operandi
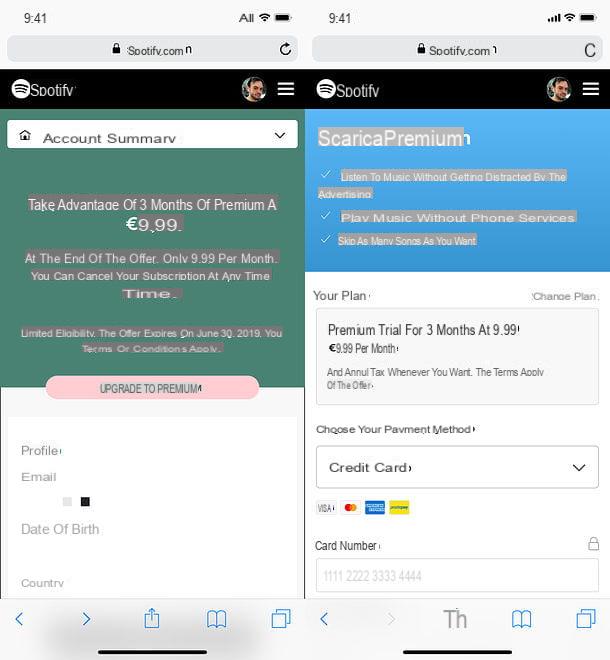
In the case of the SMS that is currently circulating, the famous Chrome update is carried out via an APK file. As a reminder, this is an installation kit for Android app, outside the Google Play Store. If you download this questionable APK file and install it, the program then asks you for permission to access your SMS, your contacts, your calls, or your photos. If you agree, then you are allowing this program, which is actually malware, to collect your information and then send it to the crooks behind it. Among the information that will be stolen from you: your phone number, the serial number of your SIM card and the list of your contacts.But it doesn't stop there. The end goal of cyber criminals is to get their hands on your bank account. It is for this reason that this kind of malware is nicknamed a “banker”. Thus, a little later, inadvertently, a screen is displayed, where one can read that access to your bank account has been blocked and that it must be reactivated. A page in the colors of your bank then offers you to enter your identifiers (bank, this time) in another form. But even before that, hackers can already read your SMS remotely, and therefore recover the codes necessary to carry out online transactions from your account. Obviously, you suspect that having access to your contacts, the malware also allows hackers to send “smishing” SMS to those around you.
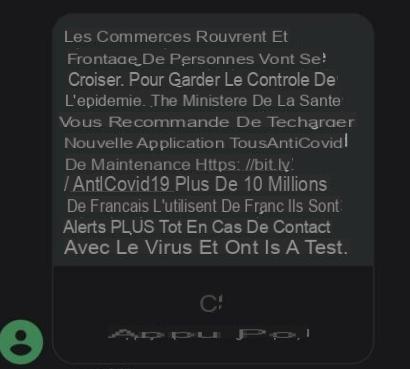
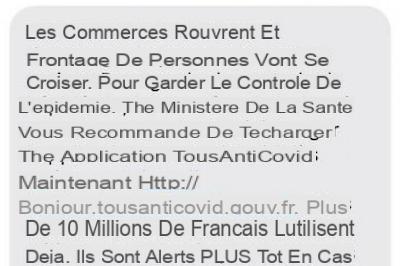
Fake text messages are of course not only linked to parcel deliveries. They exploit the news, and currently, crisis obliges, they play on this rope on several levels. For example, in August 2020, a wave of smishing targeted VSEs (very small businesses), promising them “financial assistance” in the face of the crisis. On the private side, smishing also comes from crooks who pretend to be Social Security (Ameli), for taxes, for banking establishments, for telecom operators, or for social networks. Even, for the Ministry of Health. This is what happened in December 2020: when the government had sent an SMS to all Spaniards advising them to install the TousAntiCovid application, cyber criminals had jumped at the chance, sending masses a perfect, but fraudulent, copy of this message. To do this, the hackers made a copy / paste of the official SMS, to the comma. But they inserted a link to a fake Google Play Store page, inviting the victim to install a fake TousAntiCovid app, again in the form of an APK file. This time, the objective of the malware, once installed, is to collect usernames and passwords, in order to use double authentication to hack into your bank account; but also your Facebook, WhatsApp, or Instagram accounts. According to Numerama, the malicious program, from the “Alien” family, would be able “to record everything that is typed on the keyboard, and to capture everything that happens on the screen”… As well as to steal your words password for more than 230 Android applications.
Note that another type of smishing can lead you to install genuine Trojans. As Pradeo notes, “sophisticated” Android malware sometimes pretends to be a system update, sometimes for Google Chrome (and also offers you an update). "Once installed, they can take complete control of the device and steal your data." Here too, “everything starts with an SMS” which relates to the delivery of a package…
Other fraudulent SMS finally lead to ransomware, or “ransomware”. In July 2019, ESET researchers echoed an Android ransomware campaign spread by the victims' address book. This “new family” of ransomware, Android/Filecoder.C, is based on sending fake SMS. Filecoder encrypts a wide variety of files (.jpg, .doc, .xls, .zip, .rar, .mp4, .mkv, .odt…), and demands, as you can imagine, a ransom (in cryptocurrency) against the key to decrypt and open them.

Know how to spot a fake SMS
Do not imagine that all smishing SMS are full of spelling mistakes, and therefore easily spotted. As the Cybermalveillance.gouv platform points out, messages are now much better written, and increasingly difficult to detect based on their grammatical construction. Even if, in fact, most of these fake SMS have slightly strange formulations, which do not ring true; as if they were translated from another language. We therefore cannot recommend that you nevertheless look for spelling and grammatical errors and convoluted formulas.
Also beware of text messages that use terms such as “inform” or “urgent”. Smishing text messages are based on the sense of urgency, which pushes you to act without thinking too much. Don't necessarily delete the message, but close it (without clicking the link, of course) and take a step back. If after about twenty minutes, you really have a doubt, you would do well to simply go to the site on which you placed an order, or more generally to the service supposed to have written to you. In order to check directly if a package will really be delivered to you, or if your Facebook account has been compromised.
Be aware that at no time will a delivery service force you to download an application to track your package, and even less from an application from a source other than the Google Play Store. Similarly, Facebook will never send you an SMS with a link to ask you to identify yourself… It's the same thing if the message seems to come from Ameli, or from taxes: the public authorities will never contact you by SMS. Also, beware of requests for personal information too: by e-mail, it's already weird, but by SMS, it's even more dubious.
Beware of links
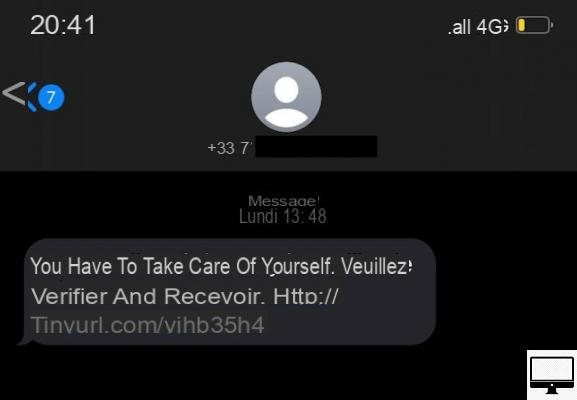
Another way to spot these fake SMS is precisely to look at the link to which it refers. In the case of fake package delivery messages such as the fake TousAntiCovid app, just like in the case of Filecoder ransomware, the URL used is not only different from the official URL, but it is also a link shortcut. Created via Bit.ly and Tinyurl.com, in this case. Two consumer services that reduce web addresses that are too long for a message to fit within the character limit of a tweet or an SMS. But do you really imagine the government, the Post Office, or even FedEx, using link shorteners?
It is also possible to test the legitimacy of any link without having to click on it. Several services indeed offer to know if a site is suspicious without going to it: just copy and paste the address of the link on Ushorten, urlscan.io, or even VirusTotal.
Do not install APK
Obviously, the fact of offering to install an APK file, therefore not validated by Google because it is external to its Play Store, is another strong signal. What should also put you on the alert are the authorization requests for the app you are about to install. Does she really need access to your text messages and contacts?
As a general rule, it is better not to install APKs, especially when you are not at all in the initiative. Because one time out of two, beyond smishing, keep in mind that an APK will be corrupted, and that malware will hide behind it.
Be careful, finally, when you are offered an update: it is better to get into the habit of checking for updates to your device directly in the settings, just like those of your apps directly in the settings. Using an antivirus can also be useful to limit the risks. But the easiest way is to activate automatic updates, and keep your device and apps up to date yourself.

If you've had a smishing bite
Did you click and install an APK, or fill in some personal info? If this is the case, notify your bank and the service linked to the identifiers provided. Then uninstall the infected app: that's enough to get rid of it. If the malware has taken on the appearance of Google Chrome, look at the size of the application: malware weighs only a few kilobytes, while the real app is several megabytes.If you want to take as little risk as possible, you can finally reset your smartphone to factory settings. Then change the passwords of all your accounts, including those of your online bank. And don't forget to warn your contacts that they may receive a scammed SMS...
Report the phishing attempt
Finally, faced with the scourge of phishing, it's up to you. Reporting platforms have been set up by public authorities and telecom operators, and they do not only concern e-mails. Thus, if you have received a fraudulent SMS, or if it seems to you to be, do not click on the link, do not install anything, and report this message on Internet-Signement.gouv (PHAROS). Or forward the SMS in question to the number 33700. By acting on your level, you may save someone else from having a bad experience. And you will also receive less fake SMS in the future, who knows.